Yay!! I finally own one for myself. Good old eBay got me a bargain, This 877 and a 837 for $280 (including postage) not bad seeing the 877 sell for over $1000 new. I think the market is getting flooded with these now, as ebay have them for around this price almost all the time now.
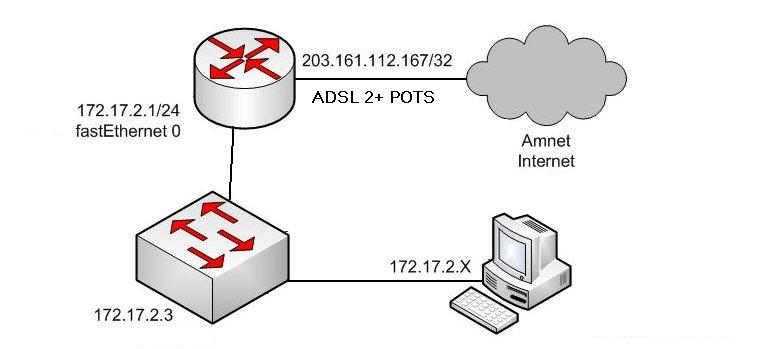
I’ve got it to a super stable connection now. I needed to phone amnet and get my port slowed down, looks like my cheap modem would just settle at a slow speed and would be happy. Where as the cisco would push for high speed until it started losing packets, but wouldn’t reset.
So I was getting the below errors
*Mar 13 11:21:34.008: atmsar_vc_tx_start(8272D204).
*Mar 13 11:21:34.008: ATM0:atmsar_dequeue_pak, dequeued a pak = 0x82330F70
*Mar 13 11:21:34.008: atmsar_transmit_pak_wrapper: deq(82330F70). vcd: 1.atmsar_transmit_pak_wrapper : encap = Data
*Mar 13 11:21:34.032: ATM0:atmsar_dequeue_pak, dequeued a pak = 0x825E1234
*Mar 13 11:21:34.032: atmsar_transmit_pak_wrapper: deq(825E1234). vcd: 1.atmsar_transmit_pak_wrapper : encap = Data
*Mar 13 11:21:34.036: ATM0:atmsar_dequeue_pak, dequeued a pak = 0x825E2418
*Mar 13 11:21:34.036: atmsar_transmit_pak_wrapper: deq(825E2418). vcd: 1.atmsar_transmit_pak_wrapper : encap = Data
So I was a bit worried for a while that I had brought a dud. But everything is looking good now. I’m going to have a bit more of a play with my config then I will post it so every one will know what settings work perfectly on the amnet network.
Goes well with my Cisco WAP4410N wireless access point doesn’t it.